MSc Thesis
Last updated: 29-7-2024
I’m currently doing my Master’s thesis entitled:
“Fault Injection Attacks on Trusted Execution for RISC-V Cores”
at the CAES group at the University of Twente.
Motivation Link to heading
As the RISC-V Instruction Set Architecture (ISA) grows in popularity, it becomes a greater target for malicious behavior. When RISC-V cores are deployed in embedded systems (which is currently the main use case), there is often a need for facilitating secure firmware updates over the air, which can be achieved by Trusted Execution. However, embedded devices often operate “in the field”, which makes it possible for an attacker to physically attack the device, for example by messing with the supply voltage or the clock signal. This is commonly referred to as a Fault Injection (FI) attack.
Therefore, this research focuses on uncovering the security implications of applying an FI attack to bypass Trusted Execution on a RISC-V core.
What is Fault Injection? Link to heading
I will write a proper article here when I find the time. For now, I found a nice illustration that encapsulates the concept of voltage glitching to perform a fault injection (credit to VoidStar Security):
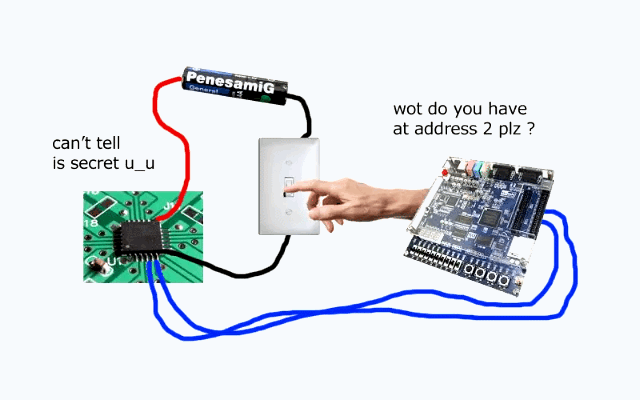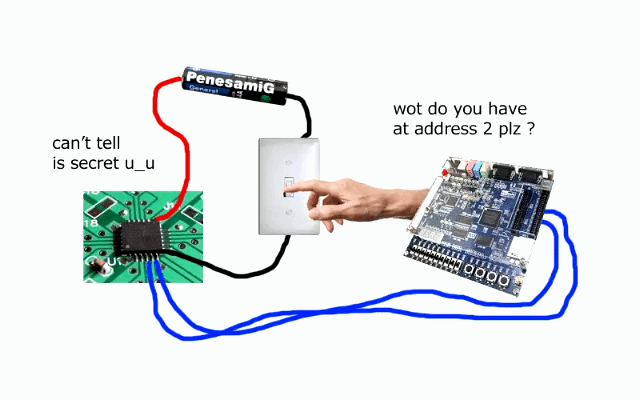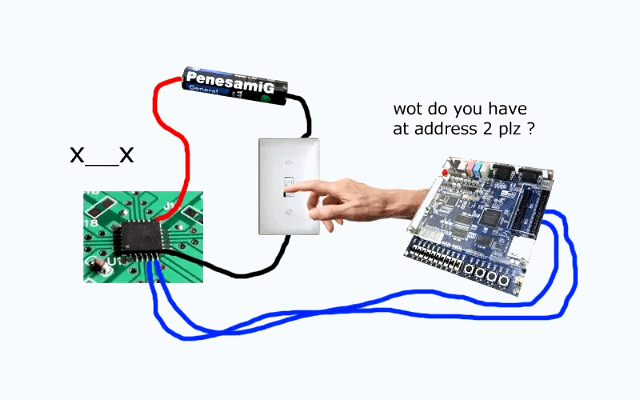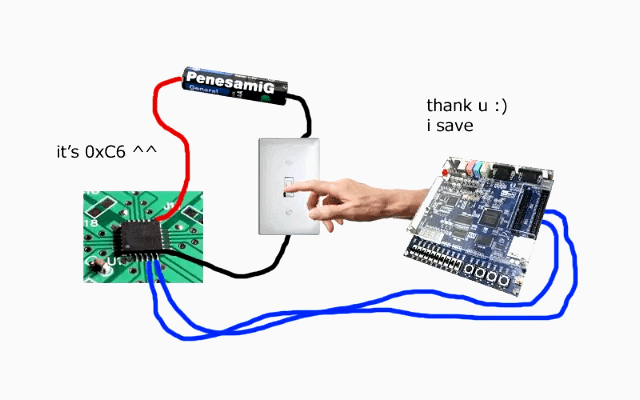
To perform the physical FI, I use the ChipWhisperer-Lite. For my purpose, it is essentially an oscilloscope with the ability to insert a specific glitch in the clock or supply voltage, with the goal of causing a hardware fault.
I use it in conjunction with either the CW308 (ASIC) or the CW305 (FPGA) to deploy a target chip.
What is Trusted Execution? Link to heading
A Trusted Execution Environment (TEE) is tamper-resistant software that facilitates the secure execution of untrusted software, such as an Operating System (OS) and user-level programs. It achieves this by separating untrusted applications from each other in memory, often by using hardware-enforced mechanisms such as privilege modes and memory protection, for example using RISC-V’s Physical Memory Protection (PMP) extension.
RISC-V Link to heading
What is RISC-V? Link to heading
For my attack target, I’m using hardware that implements the open RISC-V ISA. This is a comparatively new ISA which has a great advantage over other currently existing ISAs, such as x86 and ARM. Namely, its open-source nature, which allows anyone to design their processor around it with no restrictions imposed by some governing organization.
I am personally a big proponent of RISC-V, as it brings a level of freedom to the hardware world that has not been seen before.
In order to make it even more competitive with existing ISAs than it already is, I’m not only aiming for interesting results in my thesis, but I’m also actively searching for opportunities to advance the RISC-V ecosystem.
Why do I use it? Link to heading
Since RISC-V chips are steadily gaining a significant foothold in the embedded space, fault injection attacks are becoming a serious threat. Even though a lot of research has been done in the field of fault injection using more established ISAs, such as ARM and x86, RISC-V is still lagging behind in this respect. By using RISC-V in this thesis, my aim is to improve the state of the art for fault injection attacks on RISC-V cores, bringing it closer to the standard of other architectures.
Preliminary Results Link to heading
So far, I’ve managed to replicate the state of the art and already have already made a small contribution by doing so using my own PoC-TEE (see below) and using a different RISC-V implementation.
Proof-of-Concept (PoC) TEE Link to heading
I implemented my own PoC-TEE for a commonly used embedded RISC-V processor, namely SiFive’s FE310. It is a very minimal implementation of a monitor (machine-mode) that switches between two applications (user-mode) and prohibits them from accessing each other’s memory by using PMP.
Unfortunately, I cannot yet publish the source code. For reference, a somewhat similar implementation can be found here. The research that this implementation was used for also happens to be an important piece of related work.
The Attack Scheme Link to heading
In this research, I consider the attack performed by Nashimoto et al. to be the state of the art.
A small, but tangible contribution I’ve made is to remove one step from the scheme, namely the Side-Channel Analysis (SCA). To determine the glitch timing, Nashimoto’s approach requires the use of an electromagnetic probe to measure when the targeted instruction happens. On the other hand, my attack only requires a measurement of the timing by inspecting performance counters. It could be argued that this is an improvement, as my proposed attack scheme requires less effort from the attacker and does not require specific hardware to measure EM leakage.
However, I have found a small complication with this recently, which makes the approach invalid on certain cores. Due to a (small) change in the firmware going from a “profiling” version (where the cycles are measured) to a “real” version (where the timing found during profiling is used), the timing changes drastically and unpredictably, possibly due to instruction caching behavior. I suspect that this will be the case for certain boards where the core’s instruction memory is very slow (in this case it’s NOR-flash, which is slow), but it may still be applicable in other cases.
In conclusion, there is a persistent issue of timing, for which a number of techniques are possible (such as template matching on power traces). However, in the interest of time I will not be focusing on this, as applying one of these methods would not be a significant research contribution, as the techniques are well-researched and do not differ significantly across architectures.
Future Steps Link to heading
The next step in my research is to apply the proposed attack scheme to the Ibex RISC-V core, deployed as a soft core on an FPGA. This core implements specific hardware countermeasures against FI and SCA, so it will be interesting to see the success rate compared to a core where physical attacks are not considered during its design (i.e. the FE310).
Publishing Link to heading
In due time I will, together with my supervisors, discuss the possibility of presenting a condensed version of this work at either the Design, Automation and Test in Europe (DATE) conference or the IEEE European Test Symposium (ETS) in the first half of 2025.
In any case, the full thesis will be publicly available soon (aiming for end of October 2024) on the thesis index of the UT.